Ok, i’ve just had my hands on Windows 7 Beta DVD (thanks to Rizal from MS). I took some time to test the base operating system and try to put a review up in here for those who are interested to know what’s installed for this new operating system from Microsoft.
Summary
Ok, in a few words, Win7 is like Vista on steriods. Faster, slickier and more customizable than Vista is and probably will ever be. From installation, boot to user interface and response time, i was fairly impressed. Windows 7 is far sexier. Vista attempted to be pretty but sacrificied performance, Windows 7 has a fine balance of both. Security wise, it creates an environment more customizable and user friendly and not scare people off like what Vista did sometimes. So, Windows 7 achieved a nice balance here too.
NOTE: This review is a standalone Windows 7 review without having enterprise features such as Active Directory integration, Network Access Protection, Centralized management etc..
Ok, here’s what i was running.
- 784MB Ram
- 2 Processors enable
- VMWare 6.5.1
Please note the recommened specs for running Windows 7 and downloading beta can be found here
I used a VMWare Workstation, it’s not the best platform to evaluate an operating system. I am referring to testing Vista on VM which was slow like helllll….
Ok, so the installation starts with a nice impressive screen. Took me roughly 45 minutes to finish it all. Screenies below:
Ok, as i said, in 45 minutes flat, i’ve got to login and use the OS. First thing when i finished installing, i had 3 important updates available already so i downloaded and installed them. The version i was running was built 7000.
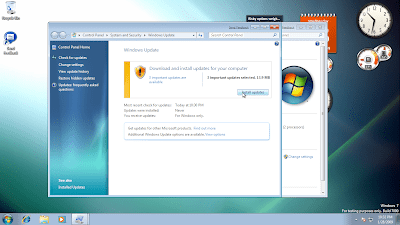
So as seen in the screenie above, obviously there was some more work done after the public beta was made available. Out of those 3 updates none for the operating system itself. The only one from Microsoft itself comes for Media Player which some decoder renderation corruption fix.
So, then i launced Internet Explorer, yes, IE 8 is installed by default (version beta 8.0.7000, RC1 wont install on Windows 7 for streamlined testing purpose). IE8 is significantly faster (warm and cold start time) compared to its predecessors. The features do make the internet a little bit more safer (check this review on IE8) .
Points to note on IE8 i personally liked
- Cold and warm starts faster than Google Chrome
- Uses much less memory than Firefox
- When freshly installed, it will present a wizard to take you through securing and personalizing IE
- It has a “Safety” tab which you can access to quickly do stuff like clear history and turn on safe browsing feature called Smart Screen.
- InPrivate browsing (like Chrome’s Incognito Mode) – Allows to lauch a new windows but nothing gets cached, remembered etc (normally used for browsing porn etc..haha
Alright, lets look at Windows network security a little. I ran an NMAP on the out of the box install of Windows 7 with the following nmap command arguments:
Nmap scan: nmap -PE -PA21,23,80,3389 -A -v -T4 192.168.11.128
NMAP couldn’t identify the OS fingerprint well simply because Windows firewall was turned on. So, i set my network location to be Home (thus relaxing the firewall setting etc). I ran the NMAP scan again and the only thing that poped up was this:
This is what Nmap found: 5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
Which was not too bad considering UPnP is probably used to connect to other Windows machines to share music etc.
So, by design, Windows Firewall was turned on and even in “Home” mode, no risky services was published out. Which i thought was better than XP (Vista had it the same also)
So, now i turned off the firewall completely and ran the same scan/test:
Nmap found the following ports opened.
- Discovered open port 49153/tcp on 192.168.11.128
- Discovered open port 135/tcp on 192.168.11.128
- Discovered open port 445/tcp on 192.168.11.128
- Discovered open port 49155/tcp on 192.168.11.128
- Discovered open port 49154/tcp on 192.168.11.128
- Discovered open port 139/tcp on 192.168.11.128
- Discovered open port 5357/tcp on 192.168.11.128
- Discovered open port 49152/tcp on 192.168.11.128
- Discovered open port 49156/tcp on 192.168.11.128
Those ports all are RPC/UPnP ports and are normal on Windows. By turning off the firewall, i couldn’t find any other “weird”services running. NMAP discovered the OS to be Windows Vista SP0 or SP1 or Windows 2008 in its finger printing. Through NetBIOS we could find (of course) its Windows 7 7000.
Then i ran Nessus with latest plugin update as of 29 Jan 2009. The scan with all options enabled and with SMB password provided yielded almost the same result as Nmap. There were no vulnerabilities (probably none developed for Nessus yet) discovered for now and thus the it had 0 high, 0 medium and 22 low (10 open ports were found). The 22 low ones are service enumeration from NetBIOS. But of course. Nothing was discovered again when the firewall was turned on.
Note: Hundreds of scans were performed through Nessus including DoS attacks, common exploits, etc..
Ok, moving out of TCP-IP, i was poking around with a few more features of security that might be of interest to you:
Security that i liked in Windows 7:
- Microsoft delivered as promised – Windows 7 does come secure out of the box with enabled UAC, firewall, IE’s Protected Mode, Action Center etc…
- Action Center – This combines all the security related tasks under one roof like Firewall, Malware protection, Restoration Points, backups, User Access Control, Troubleshooting these that i’ve just mentioned.
- Bitlocker now supports encryption of removable drives! (Finally!)
- UAC – UAC or User Access Control now can be customized to four settings basically to reduce any annoying messages from Windows that may look pretty serious and malicious but in actual fact you were just changing IP (like what happened in Vista..pff)
- Windows Vault – Where you can manage clear passwords, certificates and other Windows passwords within this vault therefore removing the need to install 3rd party tools
Well, there you have if (for now). I hope to get more apps installed and i hope to post the results of my outcome here as well.Cheers!

That is a lot of potential attack vectors.
There really isn’t a good reason they should be running and therefore open by default. These sorts of services running by default(which means 99.9% of Windows users won’t know they exist, or even how to find out) are just more targets.
I guess Michael Howard is still being ignored. I can’t count the times I have read something of his that talks about reducing the attack surface.
There is no reason to have ports open to allow sharing of files by default. If someone wants these services, then they can enable it. This is insane.
MS like usual ignores security.
I agree that the attack surface is to be reduced or even given an option to the user. I think Windows tries to make things “simple” at the same time secure enough. Its tough to achieve the right balance. But i must still yet agree with your comments about the attack vector.